Friday, 27 November 2009
Safe mode
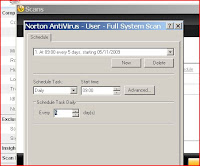
Scheduling set times for maintenance
Hardware maintenance

- Clean mouse (ball and rollers) checking for wear.
- Clean keyboard, checking for stuck keys.
- Clean monitor screen.
- Clean printer.
Tasks that should be carried out on a monthly basis are:
- Clean outside of case
Tasks carried out annually are:
- Check motherboard.
- Clean adapter cards.
The tasks that are listed above are all tasks that need to be carried out to keep the hardware clean and safe to use. If the hardware components are not cleaned when they need to be cleaned, this may cause things like dust collecting on the components and damaging them. To clean them, use cleaning equipment such as a soft lint-free brush. This can be used for cleaning glass and plastic surfaces on the components. Also using paper towels if any spillages occur, cotton buds for cleaning the mouse etc, a non-static brush for the more stubborn dirt and compressed air for cleaning fans, keyboards etc. When cleaning the hardware, you must take in consideration of the Health and Safety regulations. Making sure you use an anti-static wristbands and using anti-static mats. Other things you must take into consideration when cleaning the computer components is that the computer is switched of at the wall and that you are careful with sharp edges that may be on the components. Below is a picture of a CPU fan that hasn't been cleaned. This is wrong as the dirt and dust collects on the fan and eventually the fan will stop working and the computer will over-heat.
Compression utilities
Spyware removal
Software maintenance
(M3)The effect of all the activities is that it will improve your computers performance. This is because you are sorting through all the files etc on your computer, deleting files that are not being used, sorting the space and making it more effective to use. The effects of all this is that it will make your computer run more smoothly and quickly. This will benefit the user of the computer. Also the computer will/may have more space on the computer and the user of the computer can use this to store more files that are needed instead of having files that are not being used.
General maintenance
Daily things that should be done are:
- Virus scan of memory and hard disk.
- Take backup of changed data files.
Things that should be done on a weekly basis are:
- Clean mouse (ball and rollers) and check for wear.
- Clean keyboard, checking for stuck keys.
- Clean the monitor screen.
- Clean printer.
- Delete temporary files (Disk cleanup)
- Defragmenting hard disk and recover lost clusters. (Clusters are the unit of disk space allocated for files and directories).
Monthly tasks that should be carried out are:
- Cleaning outside of the case.
- Take complete backup of data files.
Annually tasks that need to be carried out are:
- Checking the motherboard.
- Clean adapter card contacts with contact cleaner and reset.
Other things that need to be done are:
- Record and back up CMOS setup configuration (CMOS is a type of memory that does not lose its data on a power loss).
- Keep a written record of hardware and software configuration.
Other things that you should watch for is dust settling on your computer components or dirt. This could prevent the components form working properly. For example, if there was dust that settled on the inside of the computer, it could mean that the cooling mechanism doesn't work properly, meaning that the components overheat and get damaged.
Service Packs
Spyware/ Phishing
Phishing is the process of attempting to collect information such as usernames, passwords, credit card details etc. To person who is 'doing the phishing' usually pretend to be someone trustworthy, and usually contact the person through email, instant messging etc. They usually do this by asking the user to enter their details into a 'fake' website that looks almost identical to the one they are copying.
Third party software
Wednesday, 25 November 2009
Internet Security/Virus protection

When a computer/virtual machine are connecting to the network/internet, it is taking a risk. Internet security is providing protection for your computer/virtual machine's account and files from unknown users (cyber-criminals). There are many different varieties within internet security applications including anti-virus, anti-spyware, email security, browser choice. The anti-virus civers malware, viruses, Trojans, spyware, worms and bots.
- Malware is the general name for malicious software designed to infiltrate, spy on or damage the computer or other programmable device.
- viruses are programs which are able to replicate their structure or effect by integrating themselves, such as existing folders. they also usually have a malicious or humorous payload designed to threaten or modify the actions or data of the host device without consent. For example, they could delete or hide information from the owner of the computer.
- Trojans are programs that pretend to be one thing, then in reality they do something different, such as if it asks you to 'confirm your details', it is actually stealing your details for its own use. Trojans are hard to detect.
- Spyware includes programs that monitor keyboards/keystrokes or other activity on the computer system and gives the information to others without consent.
- Worms are programs that are able to replicate themselves over a computer network, and perform malicious acts that may affect the whole society/ecenomy.
- Bots are programs that take over and use the resources of a computer system over a network without consent, and also perform malicious acts and communicate those results to those that control the Bots.
Although internet security protects you form all this, there are other ways that protect you from viruses, threats etc including disk cleanup, which comes with your internet security, disk defragmentation etc. Other things that you should do to protect yourself from viruses etc are things like chexking your email, checking who they are from and if you know that person. If the email asks you to confirm your details, make sure you know that you know it is of the person and not a cyber criminal. The picture at the top of the blog shows the free internet security software that i installed onto my virtual machine. Virus protection is there to protect you from the viruses listed above and many others. The computer can be attacked by these viruses by recieving emails that contain them or when you are accessing the internet. Normally as soon as virus writers invent new viruses, anti-virus software procedures updates that cover the new viruses. There are varieties of virus products avaliable including: virus scanner software, which scans the computer when initiated by the user. Start-up virus scanner software, which runs each time the computer is booted up, however this virus software only checks for boot sector viruses. Another virus software product is memory-resident virus scanner software. This software checks incoming emails and browser documents and automatically checks the operating environment of your computer. Having the most up-to-date DAT file (data file, which keeps the protection up-to-date), scanning regularly and avoiding opening emails that may contain viruses is the best advice, however the main defence against viruses is to have an internet security that includes virus protection etc. If this software detects a virus, it may pop up with some options for you on how you can get rid of the virus etc. Virus checking software comes in many shapes and sizes, covering ones that just cover viruses, Trojans and worms; to ones that are integrated security suites that interact with the firewall and the operating system to maintain the welfare of the system. Firewalls build a protective barrier around computers that are connected to a network, so that only authorised programs can access data on a particular workstation. The user can only control exactly which software is allowed to pass data in and out of the system. For example, automatic updates might be allowed for some installed software. The purpose of firewalls is to block unwanted traffic from entering the network.
VPC

VPC-Virtual PC
There are two different types of VPCs, these are system virtual machine and process virtual machine. The system virtual machine, which is the one that i have installed, can also be called a hardware virtual machine. This virtual machine allows the sharing of physical machine resources between the virtual machines. Each of the machines run their own operating system. Some advantages of using a virtual machine are:
- More than one OS can co-exist on the same computer.
- The virtual machine can provide an instruction set architecture (ISA) that is different from the one on the main computer/OS.
- It has high avaliablility and disaster recovery.
One main disadvantage of a virtual machine is that it is less efficient as it accesses the hardware indirectly. One other disadvantage with running virtual machines on your computer is that it could slow down the computer as it takes up too much of the memory. This could occur if you gave the virtual machine more memory or if the memory on your computer is small. If the computer has a small memory, installing and running a virtual machine would mean that it would take up a lot of the memory and slow down both the virtual machine and the main computer/OS.
Installing a virtual machine using Sun VirtualBox
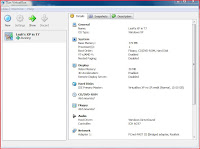 To install a virtual machine onto your computer you need to have the correct software that will allow you to do this. One software that will allow you to install a virtual machine onto your computer is Sun VirtualBox. This will allow you to install a virtual machine onto your computer from disk (if you have an operating system on a disk), through using a pre-installed version of the operating system you want to use on your virtual machine, and many other different ways. When you have installed the operating system onto your PC, you can open up Sun VirtualBox and start creating your virtual machine. You can view the details of your virtual machine including the name of your virtual machine (which you chose), the system (including base memory, processors, and boot order), display (including video memory and remote display server), hard disks, CD/DVD-ROM, floppy, audio, network, serial ports, USB and shared folders.
To install a virtual machine onto your computer you need to have the correct software that will allow you to do this. One software that will allow you to install a virtual machine onto your computer is Sun VirtualBox. This will allow you to install a virtual machine onto your computer from disk (if you have an operating system on a disk), through using a pre-installed version of the operating system you want to use on your virtual machine, and many other different ways. When you have installed the operating system onto your PC, you can open up Sun VirtualBox and start creating your virtual machine. You can view the details of your virtual machine including the name of your virtual machine (which you chose), the system (including base memory, processors, and boot order), display (including video memory and remote display server), hard disks, CD/DVD-ROM, floppy, audio, network, serial ports, USB and shared folders.
Introduction
Task 1
P5-Undertake routine maintenance tasks in relation to a PC.
P3-Demonstrate the operation and explain the use of two different software utilities.
M3-Explain the effect of the software maintenance activities carried out on the performance of a computer system.
P4-Describe the range of avaliable utility software.
Task 2
M1-Explain and implement the installation and configuration of an additional or replacement drive.
Task 3
D1-Evaluate at least three specifications for commercially avaliable computer systems and justify the one most suitable for use in a given situation.
D2-Justify the considerations for selection in the upgrade of an existing computer system.
The scenario i have been given to base my answers on is:
'You work as an IT support Technician for school in Staffordshire. A promotion to Senior Technician is avaliable. You have been asked by the head of IT to demonstrate your knowledge of a range of PC hardware and software in order to apply for this senior post. You have been asked to put a blog together showing off this knowledge'.